A Russian hacker who was found guilty of hacking LinkedIn, Dropbox, and Formspring over eight years ago has finally been sentenced to 88 months in United States prison, that's more than seven years by a federal court in San Francisco this week. Yevgeniy Aleksandrovich Nikulin, 32, of Moscow hacked into servers belonging to three American social media firms, including LinkedIn, Dropbox, and
...moreSummary
Total Articles Found: 8
Top sources:
Top Keywords:
- hacking news: 3
- Android: 2
- cyber security: 2
- Google: 2
- cybersecurity: 1
Top Authors
Top Articles:
- New Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission
- EvilGnome: A New Backdoor Implant Spies On Linux Desktop Users
- Hacker Breaks Into French Government's New Secure Messaging App
- Google Adds New Option to 'Auto-Delete' Your Location History and Activity Data
- New Android Spyware Created by Russian Defense Contractor Found in the Wild
- OpenSSH now supports FIDO U2F security keys for 2-factor authentication
- Russian Who Hacked LinkedIn, Dropbox Sentenced to 7 Years in Prison
- Zoom RCE Flaw Also Affects Its Rebranded Versions RingCentral and Zhumu
Russian Who Hacked LinkedIn, Dropbox Sentenced to 7 Years in Prison
Published: 2020-10-01 10:00:44
Popularity: 741
Author: noreply@blogger.com (Swati Khandelwal)
OpenSSH now supports FIDO U2F security keys for 2-factor authentication
Published: 2020-02-17 17:18:09
Popularity: 3094
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Here's excellent news for sysadmins. You can now use a physical security key as hardware-based two-factor authentication to securely log into a remote system via SSH protocol. OpenSSH, one of the most widely used open-source implementations of the Secure Shell (SSH) Protocol, yesterday announced the 8.2 version of the software that primarily includes two new significant security enhancements.
...moreNew Android Spyware Created by Russian Defense Contractor Found in the Wild

Published: 2019-07-25 07:16:16
Popularity: 3183
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Cybersecurity researchers have uncovered a new piece of mobile surveillance malware believed to be developed by a Russian defense contractor that has been sanctioned for interfering with the 2016 U.S. presidential election. Dubbed Monokle, the mobile remote-access trojan has been actively targeting Android phones since at least March 2016 and is primarily being used in highly targeted attacks on
...moreZoom RCE Flaw Also Affects Its Rebranded Versions RingCentral and Zhumu
Published: 2019-07-16 07:03:22
Popularity: 307
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
The same security vulnerabilities that were recently reported in Zoom for macOS also affect two other popular video conferencing software that under the hood, are just a rebranded version of Zoom video conferencing software. Security researchers confirmed The Hacker News that RingCentral, used by over 350,000 businesses, and Zhumu, a Chinese version of Zoom, also runs a hidden local web
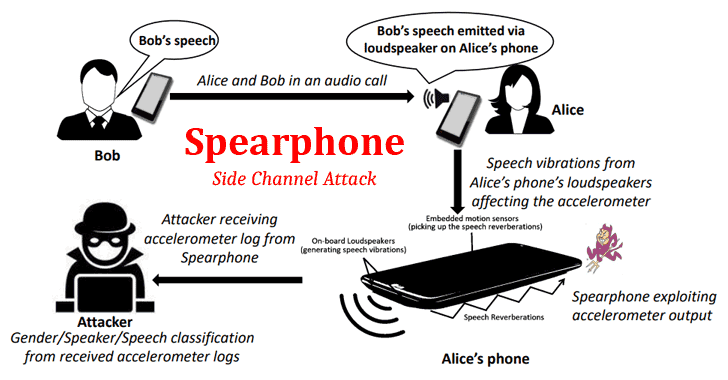
...moreNew Attack Lets Android Apps Capture Loudspeaker Data Without Any Permission
Published: 2019-07-17 10:52:05
Popularity: 7377
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Earlier this month, The Hacker News covered a story on research revealing how over 1300 Android apps are collecting sensitive data even when users have explicitly denied the required permissions. The research was primarily focused on how app developers abuse multiple ways around to collect location data, phone identifiers, and MAC addresses of their users by exploiting both covert and side
...moreEvilGnome: A New Backdoor Implant Spies On Linux Desktop Users

Published: 2019-07-17 14:13:57
Popularity: 5217
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Security researchers have discovered a rare piece of Linux spyware that's currently fully undetected across all major antivirus security software products, and includes rarely seen functionalities with regards to most Linux malware, The Hacker News learned. It's a known fact that there are a very few strains of Linux malware exist in the wild as compared to Windows viruses because of its core
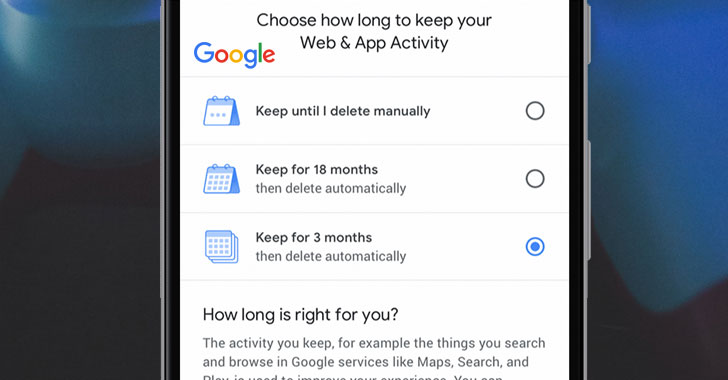
...moreGoogle Adds New Option to 'Auto-Delete' Your Location History and Activity Data
Published: 2019-05-02 07:45:38
Popularity: 3748
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
Google is giving you more control over how long you want the tech company to hold on to your location history and web activity data. Google has introduced a new, easier, privacy-focused auto-delete feature for your Google account that will allow you to automatically delete your Location History and Web and App Activity data after a set period of time. Google's Location History feature, if
...moreHacker Breaks Into French Government's New Secure Messaging App

Published: 2019-04-19 15:35:56
Popularity: 4491
Author: noreply@blogger.com (Swati Khandelwal)
Keywords:
A white-hat hacker found a way to get into the French government's newly launched, secure encrypted messaging app that otherwise can only be accessed by officials and politicians with email accounts associated with the government identities. Dubbed "Tchap," the end-to-end encrypted, open source messaging app has been created by the French government with an aim to keep their officials,
...more